Basic Concepts
- Host: Any device with a network interface which allows it to connect to other devices on a network
- Network: Two or more hosts connected so they communicate and share resources
- Switch:
- Hub:
Topology
Networks can have different physical and logical topologies, the topology defines the shape of a network
- Physical Topology: Refers to the physical layout of the wires in the network
- Logical Topology: Refers to how data moves through the network, or how the data flows through the network
- Hybrid Topology: Topology that combines two or more characteristics of some types of topology or
Types
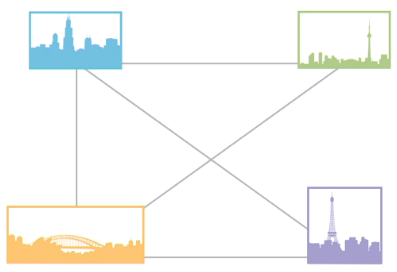
Full Mesh:
All devices directly connected to all other devices
Costly because requires multiple NICs and cables for each device connected
Provides reliability through redundancy
Example: connect WANs or large networks like cities
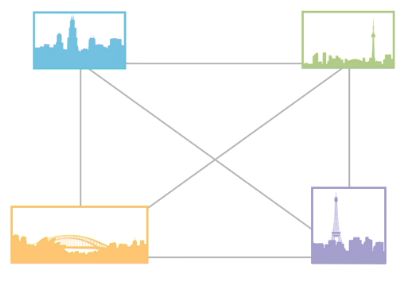
Partial Mesh:
All devices connected to at least 2 other devices
Provides strong reliability through partial redundancy
Not as costly as full mesh but still expensive for multiple NICs and cables
Example: Also WANs, like the Internet
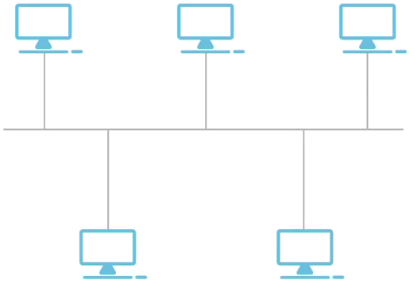
Bus:
All devices connected to a main cable called the bus
Contention is used to determine which node has access to the bus, this means the nodes content to access the bus, listenig and sendind signals when they detect the bus is available
A single damage in the cable can bring down the network
There must be access to the medium policy and collision must me handle it
Cheap and good for small number of devices (< 30 nodes)
Ring:
All devices connected to the same cable but in a circular way (ring or circle pattern)
Packets move in a ring around the network
A single damage in the cable can bring down the network
Each node has a turn to send is signal so there is no contention
Cheap but it can be slow
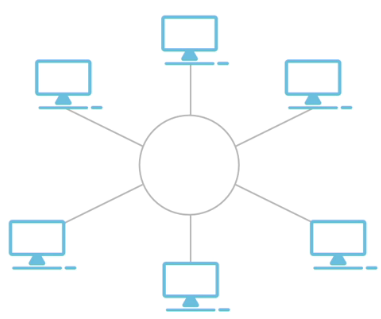
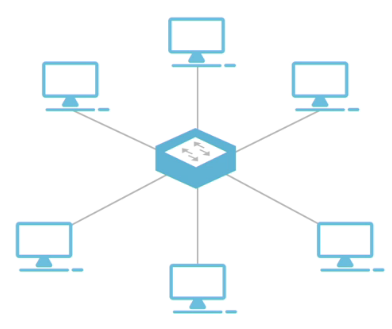
Hierarchical Star:
All devices connected to a central hub or switch
A single damage in the cable won't bring down the network
Susceptible to a single point of failure (central hub or switch)
Most common topology used in LANs
Physical Hybrid Topology:
- That contains two or more physical topologies
- E.g. Multiple star topologies where each star has a switch which then connects to a bus.
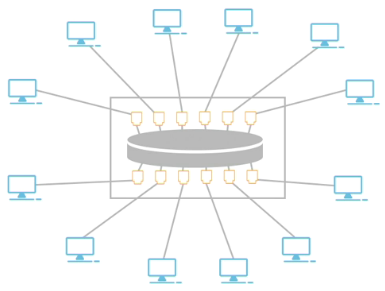
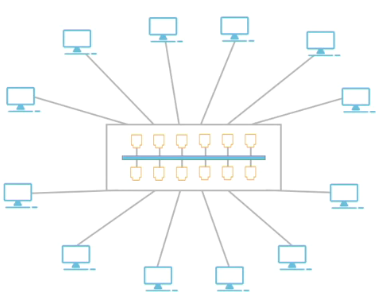
Physical-logical Hybrid Topology:
Physical topology looks one way but functions differently
E.g. Looks like a star (physical) but works like a ring (logical)
E.g. Looks like a star (physical) but works like a bus (logical)
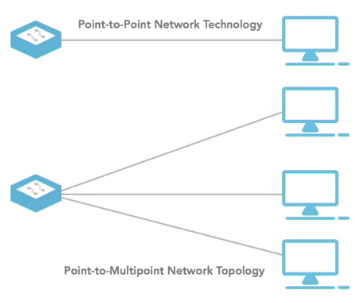
Point-to-point: Connects ONLY two devices directly to each other with NO intervening device
Point-to-multipoint: Connects a single device to multiple other devices
Network Management Models
Peer-to-Peer Network
- Every computer on the net is responsible for its own security and management
- Each computer managed as separate device by itself, management is built around individual computers
- Each device each computer handles each own security policy and security configuration
- E.g Home network or other small networks
Client Server Network
- All devices access resources through a central server
- Server are the ones that control access to the network and resources (files)
- All security is located and controlled by the central server
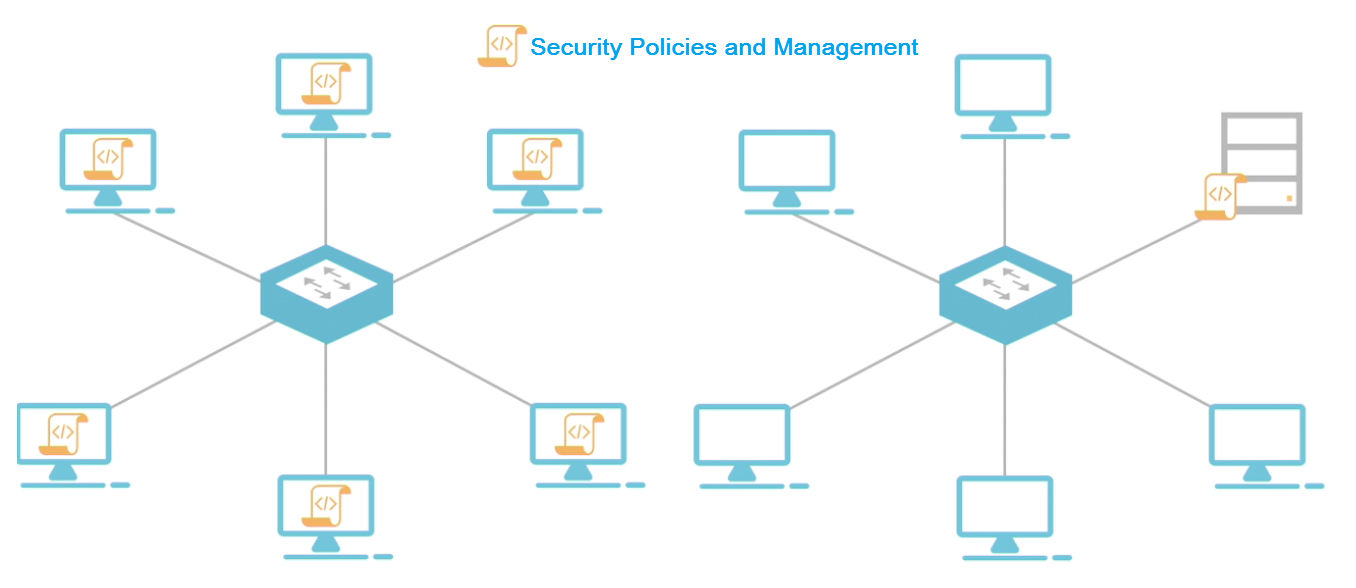
Network Physical Access
Contention-Based Network Access: Type of access to the network in which devices compete for network access
- Commonly used by Wired Ethernet
- Node listens for traffic on network if does not hear any traffic then releases packet.
- If two nodes send packets at the same time a collision occurs which can be detected by the other nodes so actions can be taken (usually this means starting random timers and attempt to transmit again once the timer expires)
- Commonly used by Wi-Fi
- Node listens for traffic on network if does not hear then releases a message to warn it will start transmitting.
- If two warning packets collide appropriate actions are taken (exactly like in CSMA/CD)
Internet is a worldwide publicly accessible infrastructure of cables, routers, switches and servers
- The WWW is not the Internet
- WWW (World Wide Web), email, FTP, VoIP, streaming video, etc. are just services that can be run on top of the Internet
Intranet is the same as the internet but private, this is usually what's used in companies
Extranet Private WANs usually own by a company or organization but that can be accessed for a fee or specifci purposes like MS Azure or Amazon Web Service (AWS)
Networks Implementations
- WAN (Wide Area Network): Network that covers a large geographical area network, it can be make up smaller networks linked
- LAN (Local Area Network) & WLAN (Wireless Local Area Network): Network limited to a small size and geographical network
- PAN (Personal Area Network): Small wireless network with more limited range (E.x. Blueetooth)
OSI (Open Systems Interconnection) Reference Model
It's a reference model that defines in general how protocols in networks all work together to carry out the job of moving data from one end to the other of the network.
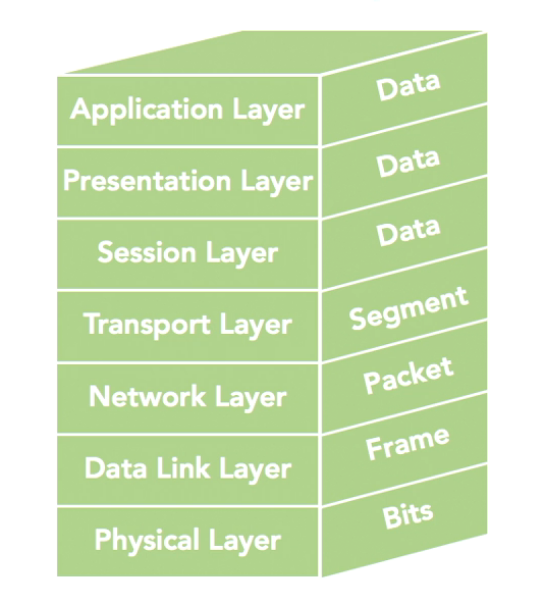
The OSI refence model has 7 layers (APSTNDP)
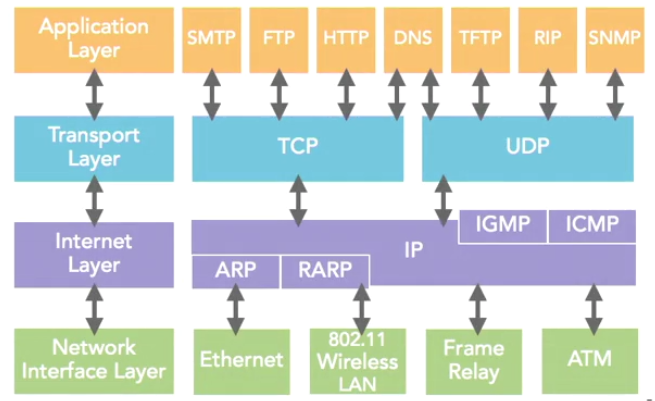
- Physical Layer: Concerned with physical transmission of raw data, defines enconding (the process of putting a sequence of character into a specialized format) and media specifications
- Data Link Layer: Concerned with providing error-free transmision from one node to the other, frame control, sequence traffic control and acknowledgment, data integrity and media access management (determined when a node is allowed to use the phy media)
- Network Layer: Controls routing (best path for data to take), subnet traffic control (like slow down messages), frame fragmentation (fragment and reassamble packets based on max frame size supported), logical-physical mapping
- Transport Layer: Ensures error-free messages delivered to destination in the right sequence, concerned with tranfer of data, segmentation of messages, message ack, message traffic control, session layers
- Session Layer: Establish, maintain and terminate sessions, security and name recognition
- Presentation Layer: Formats data to present data, data conversion or translator to standard formats
- Application Layer: Interaction with the user
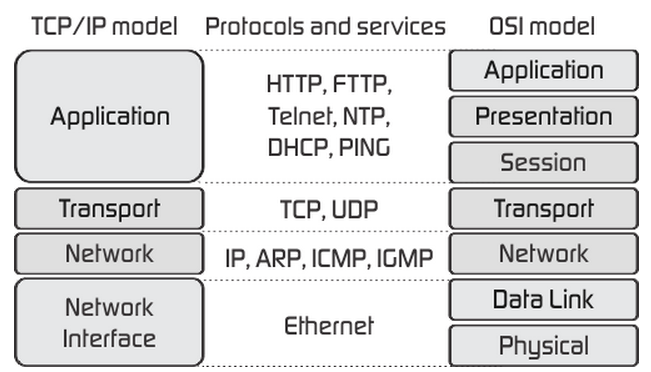
TCP/IP Suite
Group of open protocols or suite designed to work together to send data across a network. It's used by the Internet. Group of protocols that are used to connect devices together
It is the only protocol suite that is used by the Internet. Name after the two major protocols in the suite:
- TCP (Transport Control Protocol):
- IP (Internet Protocol):
TCP/IP model
Based on the TCP/IP Suite
Layers:
- Application: Defines protocols that allos programs ans user to interface with the network
- Transport: Provides Session management between hosts and status of connection
- Internet Layer: Translate to IP datagrams with source and destination information to do the routine of packages
- Network Access Layer / Link Layer / Network Interface layer: Specifies how data is physically sent through the network and defines how HW devices interface with the network medium
All the TCP/IP protocols are located on the top 3 layers
Protocols on the bottom layer are not part of the TCP/IP suite
TCP/IP Model layers and some protocols of the TCP/IP Suite
Network Devices
- NIC (network interface controller): Allows a device to access a network (works at layers 1 and 2 of OSI). The HW/NIC needs to match media (802.11x wifi), speed (Gibabit Eth) and anetwork arch (Ethernet)
- Hub: Logically function as a bus (works on layer 1 of OSI)
- Bridge: Break up network into smaller segments (works on layer 2 of OSI)
- Switches: A device used to connect multiple computers together (works on layer 2 or higher of OSI). A switch uses ports to set up point-to-point connections between devices so this avoids collisions, it can convert from one media to another (fiber to copper twistted pair),
- Routers: Moves (routes) data around the network (works on layer 3 and 4 of OSI), determine the route of packages based on the network traffic, network throughput (the amounf of data that can pass through a link), number of hops (number of jumps a packages has to go through to get to his destination), route or network reliability (route that's most likely to work), etc. They create and manage route tables with this information
- Access points: Allows devices to access a larger network, can combine the role of switches and roles
Addressing
Physical Addressing
- The actual phy address asigned to a device at factory or by HW (aka MAC address)
- MAC Address are unique on a network
- Basic MAC Address 48-bit long expressed in HEX consist of:
- OUI (Organizationally Unique Identifier): 24-bit long, manufacturer ID/specifier
- Host Portion: 24-bit long device ID/specifier
- EUI-60 (Extended Unique Identifier 60) MAC Address same as basic MAC but with Host Portion of 36-bit long
- EUI-64 (Extended Unique Identifier 64) MAC Address same as basic MAC but with Host Portion of 40-bit long and able to work with IPv6
Logical Addressing
- All devices on the network need a unique logical address which is determnied by the Network layer protocol (Like IP, almost all modenr networks use TCP/IP)
- Static: Manually, statically defined address
- Dynamic: Using protocols suca ash DHCP (requires a server) or APIPA (used by MS OS)
IPv4
32-bits IP address, 4 octets in decimal format
127.0.0.1
Still very widely used for LANs
Public Address: Obtained from ISP, one for every device directly connected to the internet, registered with ICANN
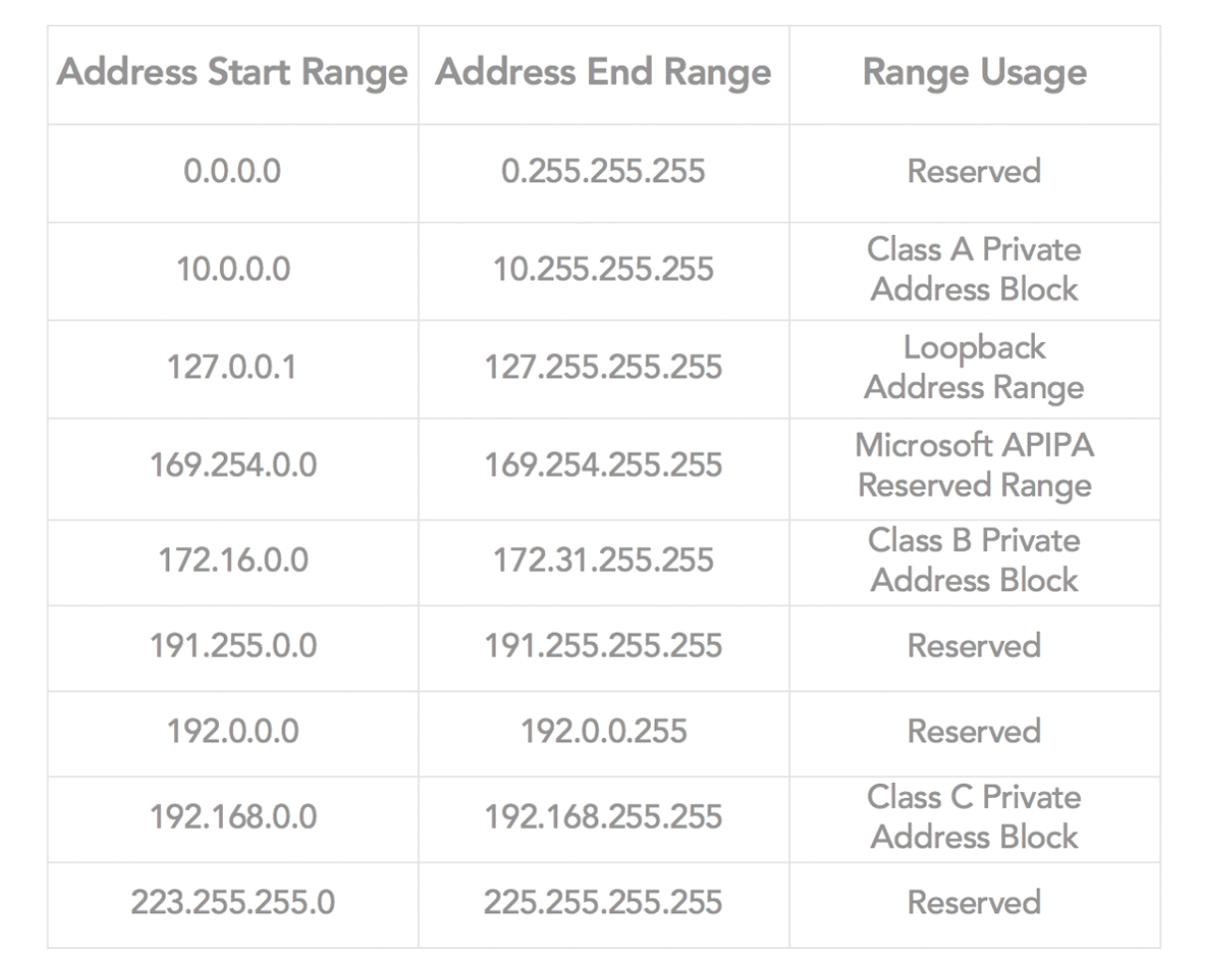
Private Address: Freely assigned in private networks (which doesn't need direct access to the internet), there are 3 ranges
APIPA:
- 10.0.0.0 - 10.255.255.254
- 172.16.0.0 - 172.31.255.254
- 192.168.0.0 - 192.168.255.254
Cast
- unicast: one device sends to another specific device, one-to-one communication
- broadcast: one device sends to all available devices on the network
- multicats: one device sends to a group of specific devices
Subnetting:
- Dividing the network into smaller networks through having common a part of the IP address
Subnet mask:
- Special IP address that is used to determine what portion of the address is used for the network and what portion is used for hosts.
- It is the AND bit mask we use to determine the subnet
- The /A prefix at the end of the IP address indicates the number of bits used for the subnet mask
- Variable Length Subnet Masks: Subnet mask used externally and multiple subnets masks are used internally
Network ID
- We never use the first IP Address for a computer since thats the network address (aka Network ID)
- IP address that identify a specific network (24 bits of IP Addr in IPv4 and 48 or 64 bits on IPv6)
Host ID:
- Uniquely identify your device in the network (8 bits of IP Addr on IPv4 and 64 bits on IPv6)
- up to 254 address since 0 and 255 cannot be used
- 0 netwotk address
- 255 brodcast address
Default Route / Default gateway:
- It is the route or address that summarizes all the locations no t on local subnet
- It offloads the responsbility of knowing all the locations to the router
- When a device doesn't know how to get to a certain device it sends the packet to its default gateway (router) the routers along the path are responsible of changing the phy address
Address Blocks: A group an IP that share a network ID
Address Space: The address IP inside an Address block
IPv6
- New header format, IPv4 routers does not understand this header so it will need to be upgraded
- 128-bits IP address (divided in 8 sections of 16-bits blocks represented in HEX) uses 64-bit MAC addresses
- Designed for efficent address alloaation and to reflect topology of the modern Internet
- Default gateway works the same as in IPv4 but it is 128-bits long
- The subnet mask is determined automatically by specifying the / prefix
- ::1 is the loopback address
- :: unspecified address which just signals abscense of address
- Compatibility Addresses: Used to allow coexistence of IPv4 and IPv6 host on the same network. Format: ::w.x.y.z
- Mapped addresses: Used to signal a note only supports IPv4. Format: ::ffff:w:x:y:z
- Global Unicast Address: Equivalent to public address in IPv4
- Link-Local Address: self configurable non-routable automatic communication on local subnet
- Unique/Site Local Address: Private Address in IPv6
- Dual IP stacks: refer to a network that has both IPv6 and IPv4 enabled on the same node
DHCP
- Dynamic Host Configuration Protocol
- Entity or protocol that configures the IP address, subnet mask, default gateway
- IP Addresses are automatically assigned using a predefined pool
-The DHCP server needs an static IP and prevents IP duplication
- DCHP server leases out (lend) IP address for a predefined amount of time after that time the client has to renew the IP lease
- Requires a DHCP server on the subnet
- Steps:
- DHCPDISCOVER: DHCP client brodcast a message to discover the DHCP server
- DHCPOFFER: DHCP server respond to show it's alive and a proposed IP address
- DHCPREQUEST: Client request information from the server (DHCPREQUEST)
- DHCPACK: server acks and sends info to client (DHCPACK)
- The DHCP server has a DHCP database of IP addresses, subnet masks, dafault gateways and subnets type that can give to clients
DNS
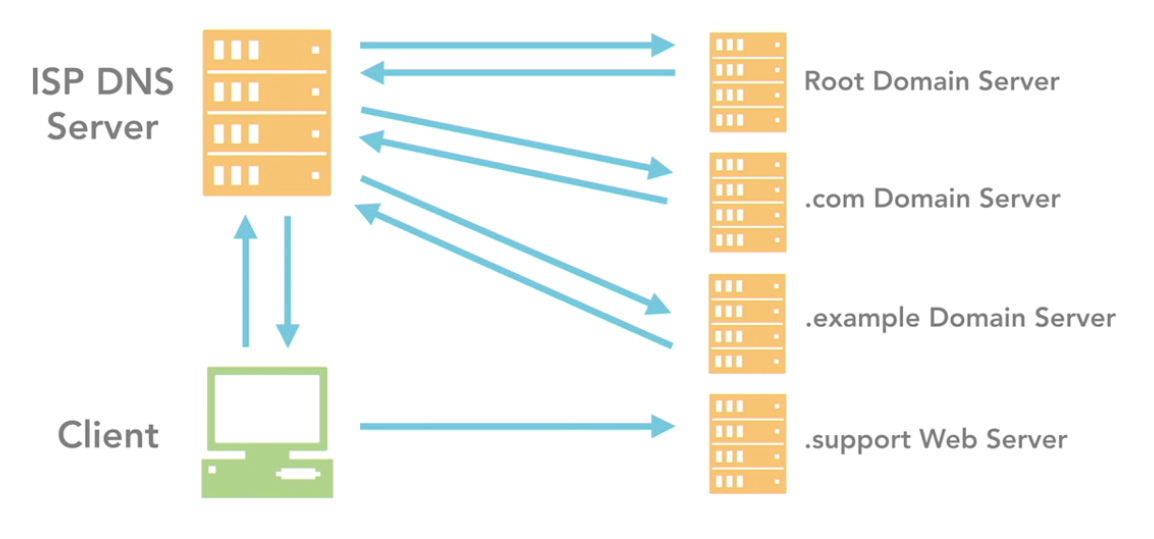
Domain Name Service / Domain Name System
It's a transalator that maps IP Addresses to names
The standard defined a tree-like structure where each branch identifies a different domain and each domain contains host names
Elements
- DNS Namespace or Domain
- DNS Name Server: The app or SW that stores and manages the domain tree structure
- DNS Resolver: client site SW that generates queries that are sent to the DNS server to find information
NAT:
- Network Address Translation protocol
- Used to conserve Public IP Addresses in Private
- Most commonly implemented by having a router that is connected to both public and private network, the router translates the packets coming from the private network to the public IP Address and viceversa
- It stores and manages a NAT table which is the one that maps public addresses to private addresses, this table is the one used to do the address translation
Port:
- Comunication endpoint, it is a logical point of communication it does not refer to a physical device or cable
- It is 16-bits number, address that is assigned to a protocol, service or process to identify it (aka port number)
- Port categories
- Well-known ports: 0-123 used to identify specific service types, assigned by IANA
- Registered ports: 1024-49151 assigned by IANA but can be purchased for specific purposes
- Dynamic or Private: 49152-65535 assigned by OS as needed
Packets: They are the formatted units of data carried accross a switched network, consisnts of control data which provides the data needed to deliver the packet and the paylod which is the actual data that is being transmitted
Remote access: it can be doen with VPN, Remote Desktop SW, Terminal emulation (command line), etc.
- Socket: is an IP address with a port number
- The internet is a WAN with partial mesh topology
- Segments also have unique network address (a segmenet which has an assigned addres is also known as a subnetwork)
- Network Segment: it's formed when a swithch connects devices to a routers interface, when routers connect to each other or connection between switches (but this is just internal network)
- Switches do NOT have MAC address because they take on the MAC address of whatever device is connected to it.
- WAP: Wireless access points
- Wi-Fi does not actually mean anything
- IPSec is a separate protocol for IPv4 but built into IPv6 (native)
- Hash is the result of applying an algorithm to data that produces a fixed length result
- http://techbus.safaribooksonline.com/video/certification/mcts/01220110017si?bookview=notes#
- VPN is a network that has the goals of providing secure, encrypted communication over unsafe networks
TCP/IP Configuration
- default gateway: where do I go if I cannot find anything
- release: release the current IP address
- renew: ask the DHCP server to get a new IP Addr
Routing
- The gateway is used to tell when we want to communicate with a device that is in a different network we will forward the packet to the dafault gateway ip address whic can be seen as the router IP address
- Routing protocols are SW that allows the router to send packets to the appropriate networks (OSPF, RIP 2, etc)
configure list of reachable networks
- Dynamically handle network changes
- Static routing: means routes and paths added manually
IPSec: Internet Protocol Security
What is IPSec and Why is used?
- IPSec is a protocol that is used to protect traffic/data.
- It adds security to the IP (Internet protocol) packets
- Its a defined standard protocol so guarantees inter operability between manufacturers
- IPSec is is used to implement a VPN (Virtual Private network)
IPSec Key services (What it provides?)
- Key services:
- Confidentiality: Encrypt traffic and Make sure only the entity we want to communicate with can read the messages we are sending
- Integrity: make sure the data is not altered by another entity
- Authentication: have a trusted communication and make sure we are talking who we really want to talk to
- Anti-replay; avoid other entity to replicate a sequence of packets to accomplish something
- IPSec uses SHA1, SHA2 for integrity, HMAC for authentication and integrity, DES, AES-CBC, 3DES-CBC for confidentiality
IPSec Main Protocols
- IPSec is actually a group of three main protocol
- Internet Exchange Key (IKE):
- Always used for key exchange of used on AH or ESP
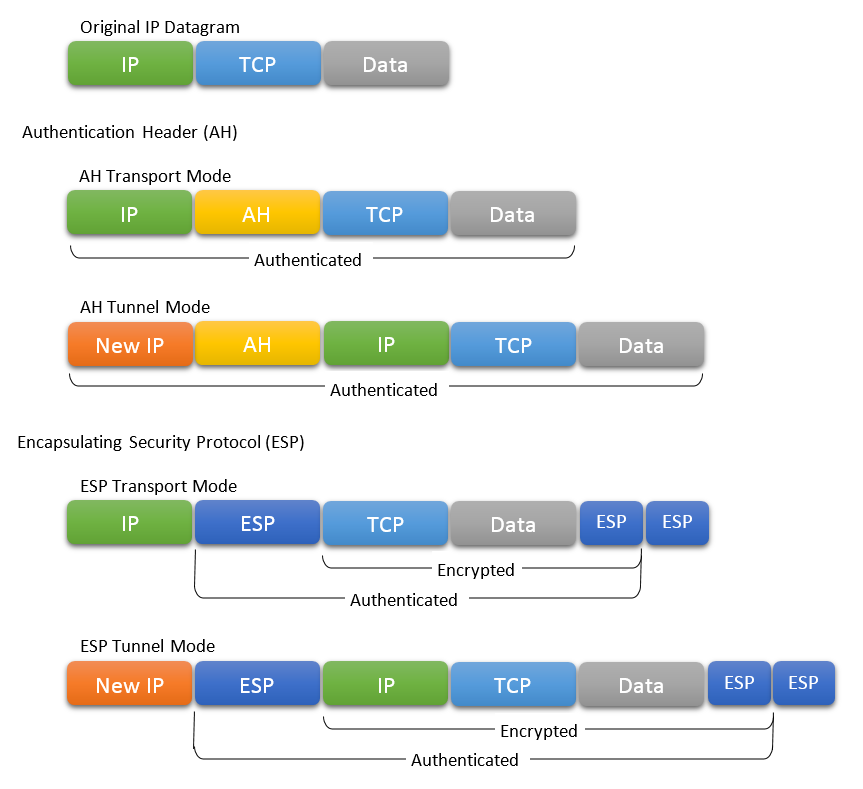
- Authentication Header (AH):
- Provided Authentication and Integrity: Used to prove the identity of devices (Auth) and to prove the data has not being modified (Integrity)
- Generates AH header that Auths and guarantees integrity of the data
- Data here refers to the data of the transport and application layers and also some fields of the IP header becasue all of this data is used to genrate the Hash, except for the IP Fields that are changing during routing
- Encapsulating Security Protocol (ESP)
- Besides auth and integrity, it provides confidentiality through encryption
- Inserts a header and tail
IPSec Modes:
- The modes of IPSec refers to the way it constructs packets with the purpose of defining the level of protection we want to give to a packet
- The protocols are independent of how they are used, modes define how the protocols are used
- Transport Mode (default Mode)
- Protects the data but not the header (you can see who is communicating with who but you cannot see the data)
- Run between used for VPNs to have a secure communication
- Tunnel Mode:
- Protect packet and header The whole packets is encrypted
- Usually used between network devices
- IP Packet is encrypted for protection and then a another header is added to form a new packet
IPSec Policy
- IPsec uses Policies and Group Polices which are Connection security rules
- IPsec policy is a list of rules that determines which traffic will be protected and what it will be done with that traffic
- Filter list determines which traffic is protected
- Filter action determines what it will be done with the traffic (Block, Permit/Allow and Negotiate Sec)
- You can create multiple policies
- Only one policy will end up being assigned to a computer
IPSec Default Group Polices
- Client (Respond only): never initiates secure communication but responds to negotiation request to establish a secure communication
- Server (Request Security): Always Request secure Traffic but accepts unsecured traffic in case client does not support IPSec
- Secure Server (Required security): Always requests secure traffic and only accepts secure communication
Security Associations (SAs)
- A security association is simply the bundle of algorithms and parameters (such as keys)
- They describe the list of protocols/algorithms a device is able to use during an IPsec communication. You can think SAs as a list of supported protocols
- SAs store the parameters and algorithms agreed during negotiation, also store information need by this algorithms like nonce, keys, etc.
- AH and ESP each requires two SAs per protocol used one inbound and one outbound
when two devices want to communicate
- SAs define the possible combinations of protocols
IPSec Authentication
- What we want is to know the devices that are going to communicate are who they say they are
- IPsec support 3 options for authentication:
- Kerberos:
- Certificates
- Preshared Key















